Yesterday, a critical vulnerability in React Server Components was announced that affects both reactjs and Vercel’s NextJs.
The vulnerability is present in versions 19.0, 19.1.0, 19.1.1, and 19.2.0 of:
and Next.js with versions ≥14.3.0-canary.77, ≥15 and ≥16.
Affected Replit applications
When created, most Replit applications are not affected by this vulnerability. But, an application could become affected if the user or Agent had previously installed the vulnerable packages above.
Only apps created with “Mobile app [beta]” option in Build mode were vulnerable upon creation. We have enabled the vulnerability mitigation in Google Cloud Armor to protect replit.app deployments of Mobile applications. We have patched the Mobile app option so new applications created with it are not affected.
We will be notifying all users who created a Mobile application by email.
Fix
To fix the root cause, upgrade your Next.js and react-server-dom-* dependencies to their latest versions.
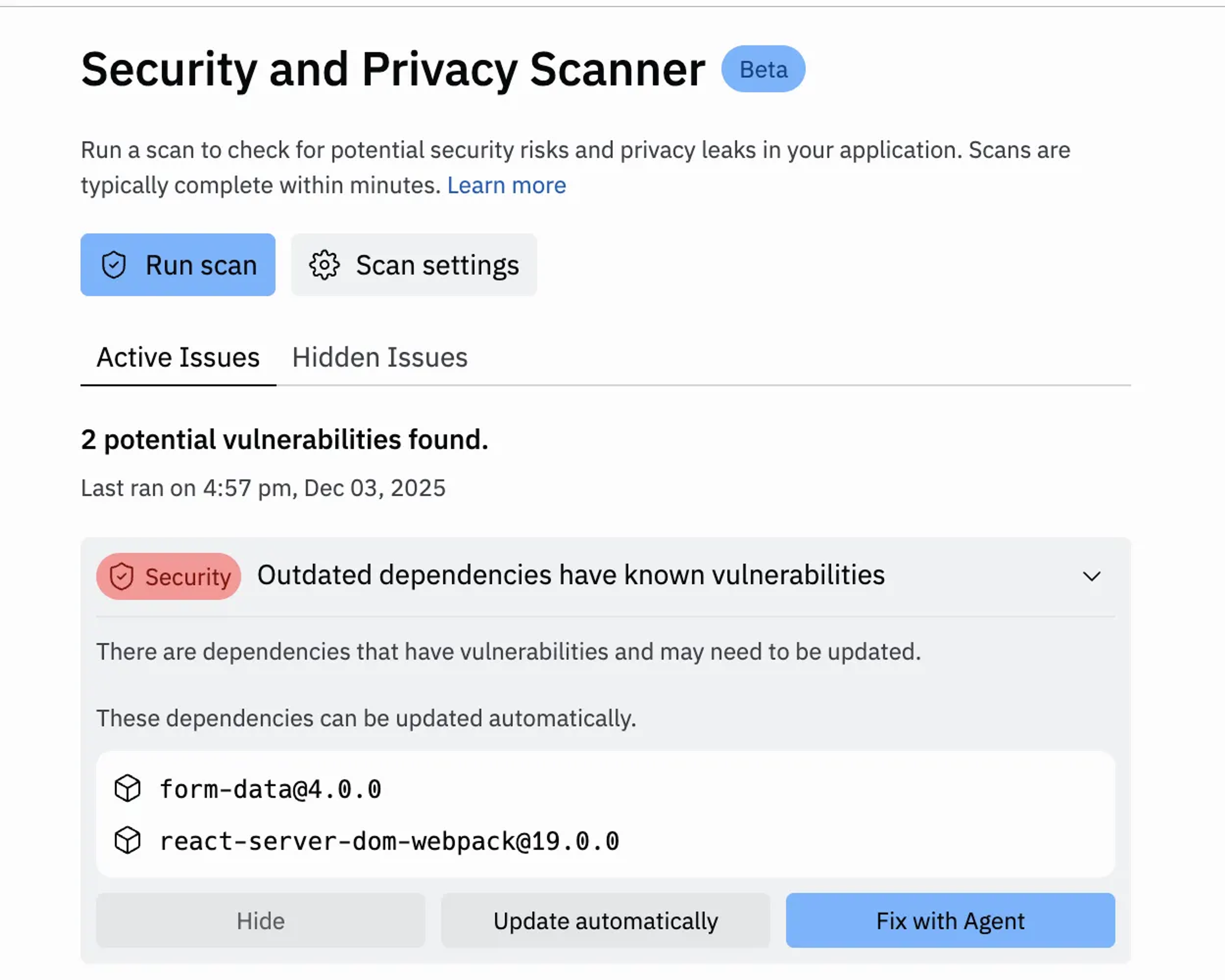
To do this open the Security Scanner in the app Workspace, click Run scan, and then Fix with Agent.
Mitigation
All replit.app publishes and repl.run preview applications are protected by Google Cloud Armor and we have enabled Google’s protections for the vulnerability. Published custom domains are also protected by this mitigation.
You can use the Security and Privacy Scanner in your app Workspace to check if your application is impacted by the vulnerability.
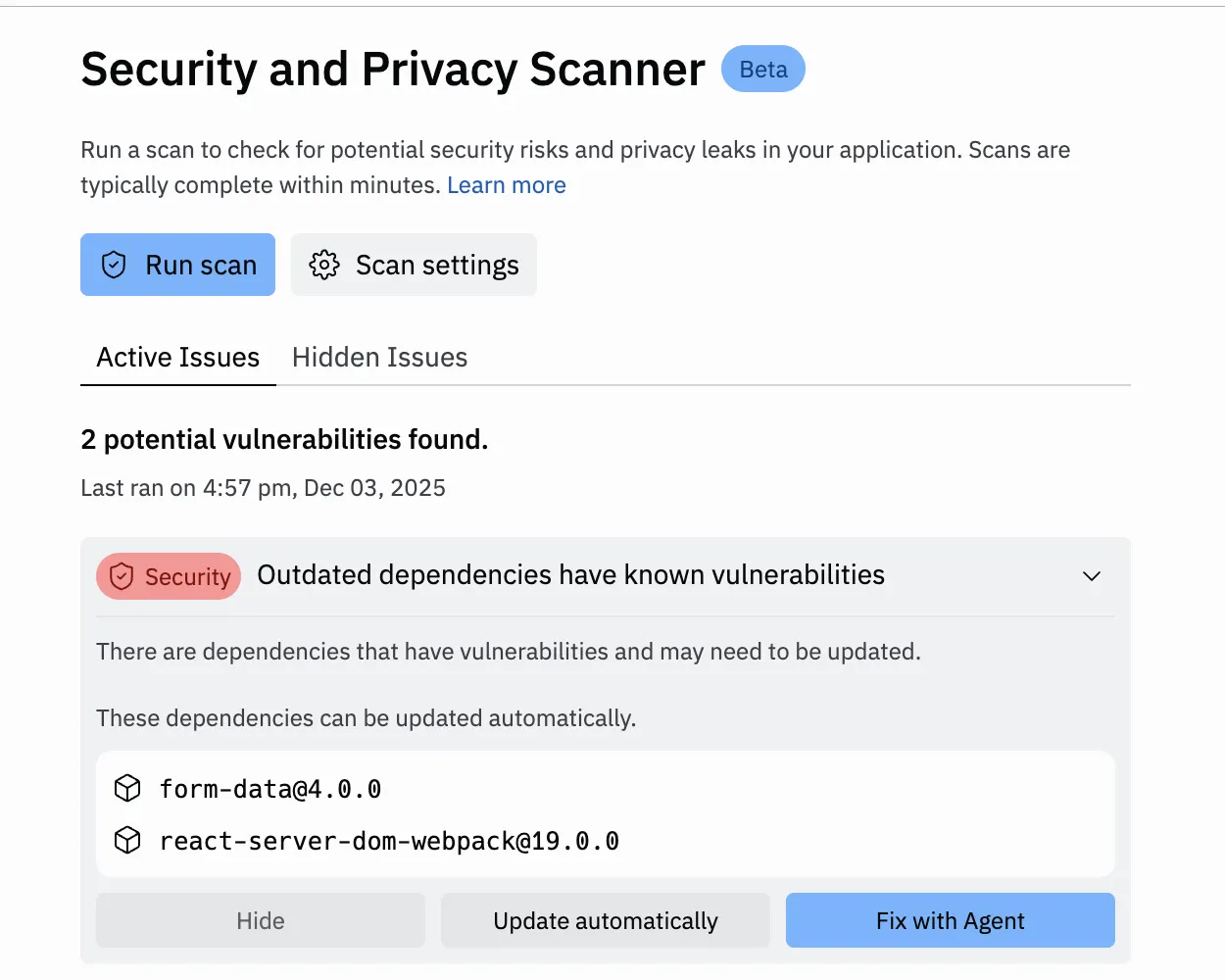
All users can enable the security scan feature while publishing to detect this and other vulnerabilities:
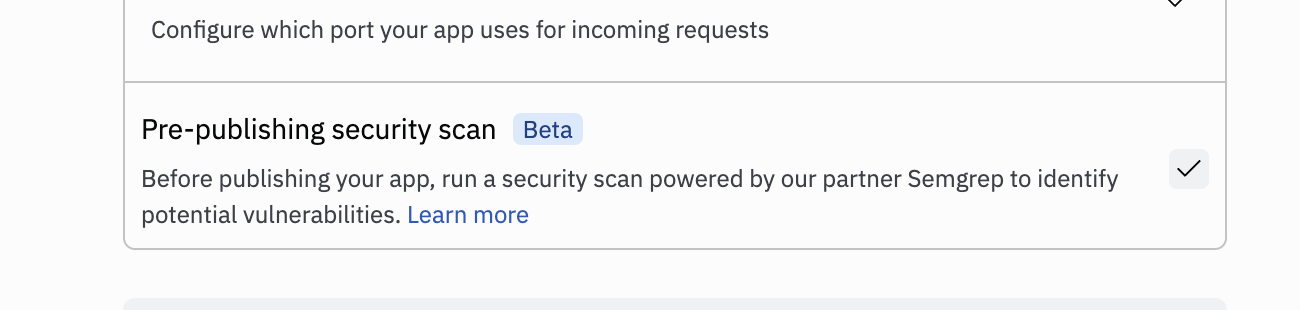
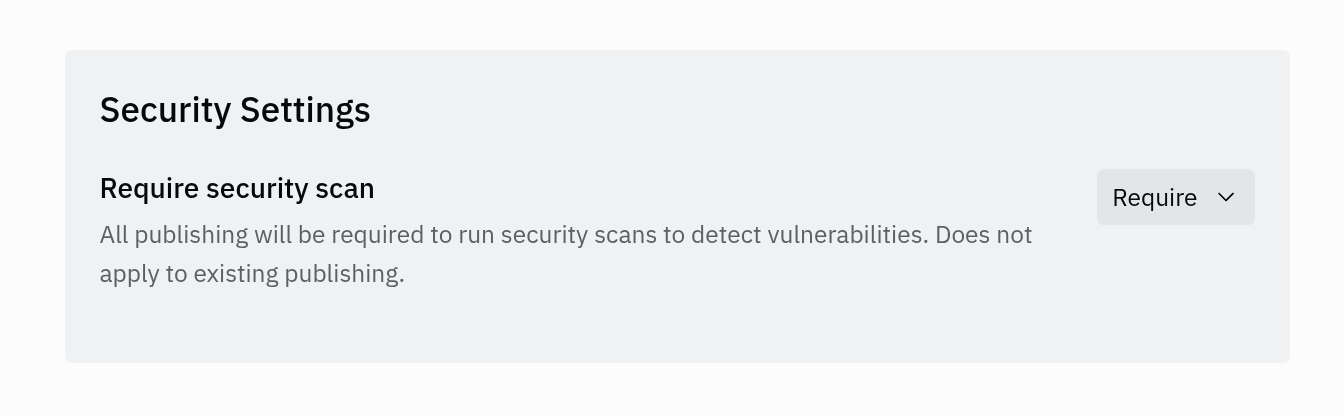
Teams and Enterprise administrators can require security scans when publishing to catch this and other vulnerabilities: